index.md 6.4KB
title: Cybercriminals pose as “helpful” Stack Overflow users to push malware
url: https://www.bleepingcomputer.com/news/security/cybercriminals-pose-as-helpful-stack-overflow-users-to-push-malware/
hash_url: 1bff60d11f
archive_date: 2024-05-31
og_image: https://www.bleepstatic.com/content/hl-images/2024/05/29/stackoverflow-header.jpg
description: Cybercriminals are abusing Stack Overflow in an interesting approach to spreading malware—answering users' questions by promoting a malicious PyPi package that installs Windows information-stealing malware.
favicon: https://www.bleepstatic.com/favicon/bleeping.ico
language: en_us

Cybercriminals are abusing Stack Overflow in an interesting approach to spreading malware—answering users' questions by promoting a malicious PyPi package that installs Windows information-stealing malware.
Sonatype researcher Ax Sharma (and a writer at BleepingComputer) discovered this new PyPi package is part of a previously known 'Cool package' campaign, named after a string in the package's metadata, that targeted Windows users last year.
This PyPi package is named 'pytoileur' and was uploaded by threat actors to the PyPi repository over the weekend, claiming it was an API management tool. Notice how the package has the "Cool package" string in the Summary metadata field, indicating it is part of this ongoing campaign.
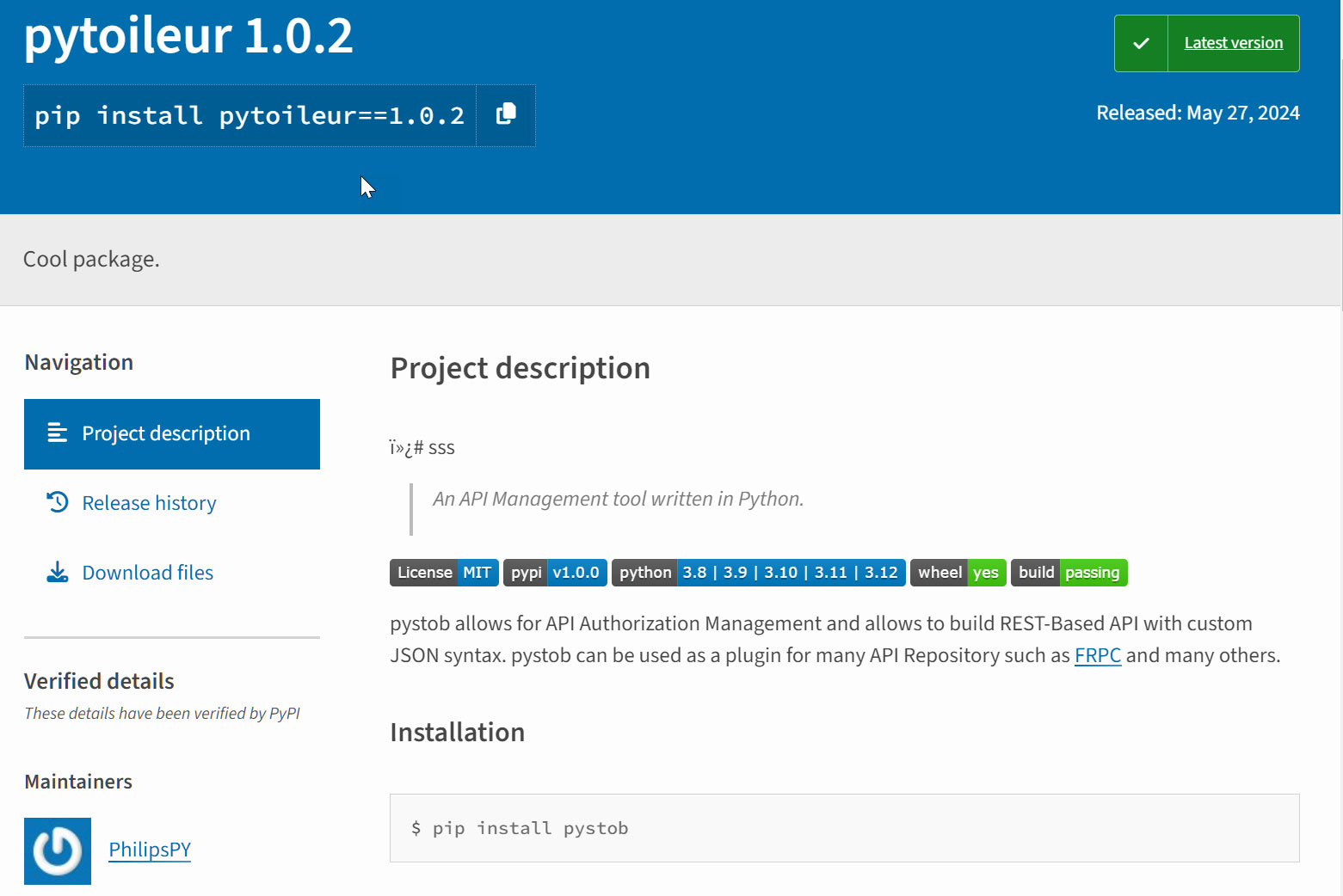
Source: Sonatype
Malicious packages like this are usually promoted using names similar to other popular packages, a process called typo-squatting.
However, with this package, the threat actors took a more novel approach by answering questions on Stack Overflow and promoting the package as a solution.
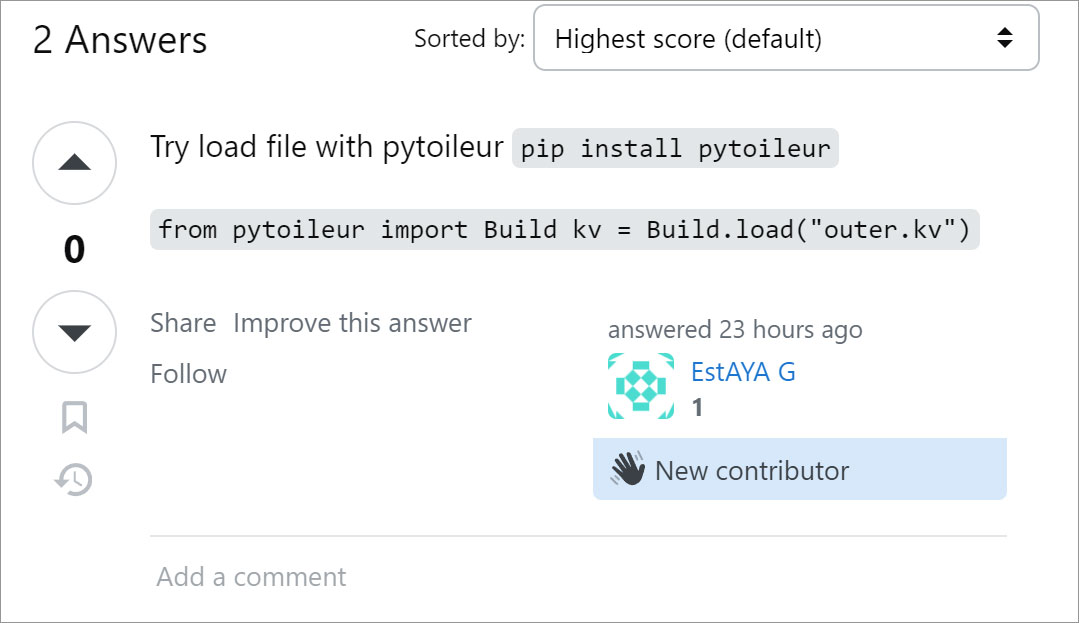
Source: BleepingComputer
As Stack Overflow is a widely used platform for developers of all skill sets to ask and answer questions, it provides a perfect environment to spread malware disguised as programming interfaces and libraries.
"We further noticed that a StackOverflow account "EstAYA G" created roughly 2 days ago is now exploiting the platform's community members seeking debugging help [1, 2, 3] by directing them to install this malicious package as a "solution" to their issue even though the "solution" is unrelated to the questions posted by developers," explained Sharma in the Sonatype report.
In this case, the pytoileur package contains a 'setup.py' files that pads a base64 encoded command to execute with spaces so it is hidden unless you enable word wrap in your IDE or text file editor.
Source: BleepingComputer
When deobfuscated, this command will download an executable named 'runtime.exe' [VirusTotal] from a remote site and execute it.
Source: BleepingComputer
This executable is actually a Python program converted into an .exe that acts as an information-stealing malware to harvest cookies, passwords, browser history, credit cards, and other data from web browsers.
It also appears to search through documents for specific phrases and, if found, steal the data as well.
All of this information is then sent back to the attacker, who can sell it on dark web markets or use it to breach further accounts owned by the victim.
While malicious PyPi packages and information-stealers are nothing new, the cybercriminals' strategy to pose as helpful contributors on Stack Overflow is an interesting approach as it allows them to exploit the trust and authority of the site in the coding community.
This approach serves as a reminder of the constantly changing tactics of cybercriminals and, unfortunately, illustrates why you can never blindly trust what someone shares online.
Instead, developers must verify the source of all packages they add to their projects, and even if it feels trustworthy, check the code (with word wrap enabled) for unusual or obfuscated commands that will be executed.
